Can I Sign Someone Else's Name With Their Permission
I think someone I know has hacked my Gmail business relationship. What should I do? Valeria
This is a relatively common question. Other recent examples include "Someone is using my Gmail business relationship to steal my data on a game. How do I become rid of him?" from Rodimus Ghost, and "My daughter is using my Gmail account. How do I stop her?" I don't recollect getting these queries nearly other e-mail services.
My usual response is: "How practice y'all know?"
There might be emails in the Sent Mail service folder that you lot didn't write, though hackers tin can comprehend their tracks by deleting copies of sent emails. However, incoming emails are not an indicator. I've had emails from Instagram, GoCompare, Barclaycard Business, Apple, Prattville YMCA and many other organisations where people take entered my Gmail accost, probably past mistake. It doesn't hateful they accept accessed my account.
The all-time way to tell if someone else has used our account is to roll down the Gmail inbox and look for "Last account activeness" in the bottom right. Clicking on Details produces a nice table that shows how someone accessed the account (browser, mobile, POP3 etc), their IP address, and the date and time. Y'all should recognise any sessions that aren't yours.
In fact, Gmail volition, by default, notify you lot of any unusual activity. You may go an alert if you lot log on with a new device or from a unlike country. These alerts tin can exist annoying but they increase your security. Don't turn them off.
Y'all can also cheque the Recently used devices page, which lists all the PCs, phones and tablets used in the previous 28 days. Once again, it should be obvious if whatever of them are non yours.
Double-check Settings
There are elementary ways to read someone else'southward emails without leaving obvious traces. These are controlled from Gmail's Settings, which you lot can observe past clicking the cogwheel in the top right.
On the Settings folio, click Accounts and Import and go to the penultimate entry: "Grant access to your business relationship". Someone could click "Add an email business relationship", enter another Gmail address, and admission your emails from that account. They can keep these emails marked equally Unread even if they've read them.
Next, click Forwarding and Popular/IMAP and review the tiptop section on mail forwarding.
Email services allow users to forrard all incoming emails to another email address, and I retrieve everyone should practice this. I have Gmail forward all my emails to my business relationship at Microsoft's Outlook.com. As a result, I tin still read and reply to emails even if Gmail is inaccessible. Farther, if Gmail locked me out, I'd nevertheless accept copies of emails going back to Apr 2004.
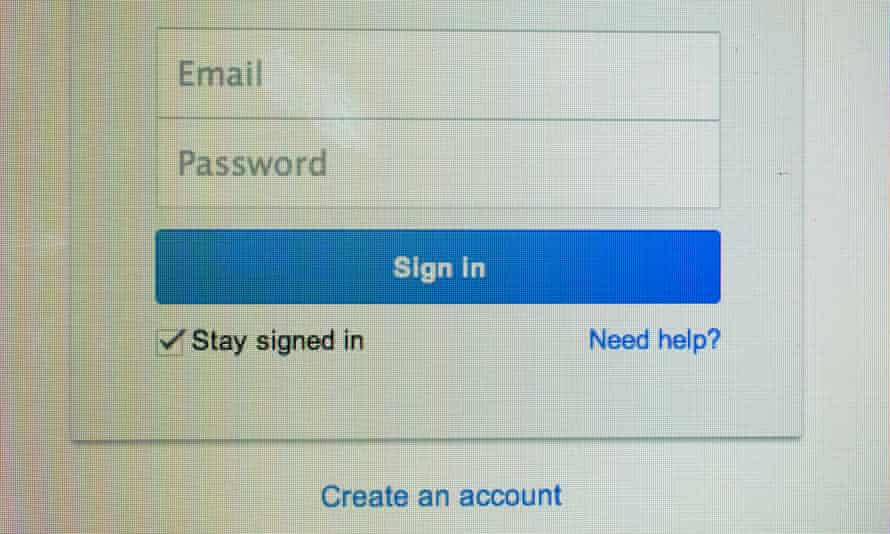
So, if you lot tin can admission someone'south mailbox, you can ready mail forwarding to an address that you control, and they'll probably never notice. Brand sure nobody has washed that to you.
If you lot only read Gmail in a web browser, you could also disable the POP and IMAP access features. This would provide a minor increase in security, only I don't recommend it. In fact, there are advantages to using a PC email plan such as Microsoft Outlook, Thunderbird or eM Client to collect Gmail using the IMAP protocol. These programs have more features than the web version of Gmail, and they store emails on your PC so that you can easily admission them offline. IMAP leaves the original emails online, and so y'all tin can still access them using different devices. (Yes, you can also install "Gmail Offline" via the Offline tab.)
Think to relieve whatsoever changes before switching tabs.
Password security
Once you are sure your mailbox is not being hacked, change your password to keep other people out.
In Gmail, become back to Accounts and Import and click "Change password".
Choose a strong password or passphrase that includes numbers and upper-case characters. Gmail requires at least eight characters, but aim for 12 or 16 or even more. Longer is better. Information technology won't be random, unless you apply a password manager, but avoid family names, names of pets, birthdays, sports teams and other obvious elements.
For convenience, your browser or email plan tin remember your password. If you allow this, your electronic mail is only as secure as your PC. Anyone who can access your PC can admission your email.
Nowadays, of course, the simplest fashion to hack someone's email is to use a phishing attack. In this example, someone sends you a link in an e-mail that pretends to come up from Google. Clicking the link opens a browser tab where "Google" asks y'all to log in with your e-mail address and countersign. The attacker harvests the results.
If you lot're going to leave your PC unattended or fall for a phishing attack, it doesn't thing how strong your countersign is.
Do the two-footstep
If someone tin access your Gmail business relationship, they can change your password and lock you out. Y'all can prevent this by using "two-step verification". With Gmail, this usually means Google will text a code to your mobile phone. This is fine until y'all don't have a betoken or lose your phone. Gmail therefore asks for a redundancy phone number. (Landlines work: you get a voice message.) Gmail also allows yous to impress out a small set of verification numbers that you tin can apply when travelling.
Google provides an alternative to SMS in the course of Google Authenticator, a free app for Google Android devices and Apple tree iPhones and iPads.
You can also simplify two-step verification slightly by using "application specific passwords". For example, if you admission Gmail via a smartphone app or an email customer that tin can't handle two-footstep verification, you tin can request a separate countersign for each e-mail program on each device. It only has to be entered in one case.
To use these extra security features in Gmail, go to Accounts and Import, click "Other Google Account settings" and and then "Sign-in & security". This provides access to password changes, two-step verification, and account recovery options.
Business relationship recovery
What if your password stops working and you tin't get into Gmail? The traditional arroyo to account recovery is to ask for some personal information, such every bit your mother's maiden name. This enabled people to hack e-mail accounts by using information gleaned from social media accounts. Y'all can forbid this by using random messages or something obscurely incorrect – "Mother's maiden name: Quetzalcoatl" – but then you accept to remember the answers.
Google's recovery options include a phone number, some other email accost and a security question. Information technology likewise likes to ask when the account was opened and when you last used it.
You may exist able to find out when you lot created your Gmail account by searching for (in my example) earlier: 2004/04/15, or whatsoever date in YYYY/MM/DD society. That won't work if you deleted your welcome message, just vary the date to find the oldest message yous can.
Business relationship recovery is the only way to get your Gmail back if yous forget your password or a hacker changes it. Simply it doesn't always work, and you may exist told that "Yous weren't signed in because Google couldn't confirm that xxxxxxxx@gmail.com belongs to you."
So – as another reader, Paul, found before this year – you end upwards in a "failed online recovery loop. No contact centre. No online chat. No contact details at all." It looks as if in that location's nothing you can practice except open up a new business relationship, change all your online passwords and electronic mail addresses, and promise nothing bad happens.
Take you got a question? E-mail it to Ask.Jack@theguardian.com
Source: https://www.theguardian.com/technology/askjack/2017/jul/27/how-can-i-stop-someone-else-from-using-my-gmail-account-security
0 Response to "Can I Sign Someone Else's Name With Their Permission"
Post a Comment